In my post yesterday on Securing a Web API, I asked how might I test my API after securing it, since I didn’t have a client app created yet.
Of course, there is a way using Postman.
I’ve mentioned previously how to use the “run now” policy feature to test your policy and review your tokens. That previous blog post used a web application. Today’s blog posts uses a native app as the selected application.
Go to your B2C_1_SiUpIn policy:
- Under Select application, chose Hello API WPF App.
- Under Select reply url, choose the
httpsurl - Expand Access Tokens and under Select resource, select Hello API (or whateer name you gave your API from yesterday’s blog post). Make sure all the scopes are selected.
Here’s what my Run Policy Settings look like.

Click Run now. You’ll see a new browser tab appear. Copy the resulting URL and open up your favorite flavor of notepad.
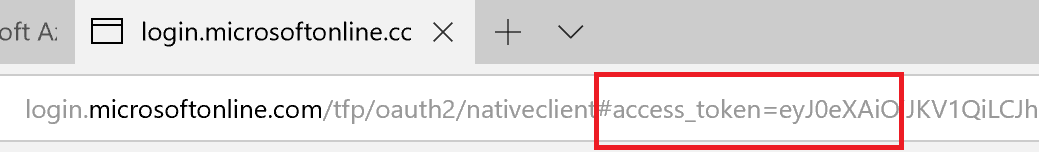
Make sure you only copy the access token and none of the other parameters that come after the access_token. This had me scratching my head for a good half-hour.
Open up https://jwt.ms and paste in the access token to confirm it all looks good and contains the claims you’re Hello API is expecting, e.g. “read”

Next, fire up Postman. Also, make sure your Hello API project is running 🙂
I’m still new to Postman, so YMMV. If you have a different way of using Postman for this scenario, please let me know!
- Choose GET and insert the URL for your Hello API /hello endpoint.
- Under Headers, type in Authorization
- For its value, type in
Bearerthen the access token.
 And if all is setup correctly, you’ll get the expected response!
And if all is setup correctly, you’ll get the expected response!
I’m still working on a blog post on how to debug all these steps for creating a client application and an API for use with B2C. Stay tuned!
“Make sure you only copy the access token and none of the other parameters that come after the access_token. This had me scratching my head for a good half-hour.”
I don’t get an extra parameters… I’m curious… What other parameters do you get?
LikeLike
for example, &token_type=Bearer&expires_in=3600.
LikeLike
oh, they are there for me too! now I see them. Thanks!
LikeLike
With the help of Chris Padgett, I got the request access token from postman working. IHMO, this approach is much cleaner. And once you get it working, much quicker. Reference: https://stackoverflow.com/questions/47275079/request-access-token-in-postman-for-azure-ad-b2c#answer-47564076
Perhaps you could explore that area some more? For example, there are 4 grant types in postman. I think we’re interested in Auth Code and Implicit with B2C but I’m not sure.
LikeLike
Ah! I didn’t know Postman had a request access token feature. Thanks for the instructions! I’ll play with it and report back!
LikeLike
Hi Sara,
In case you have a public facing API and you have number of clients consuming it, how do you get client (username) based token?
thanks,
Adeel
LikeLike
Hi Adeel – you should post a question stack overflow and tag it w/ “azure-ad-b2c”. Can you elaborate what you mean by client (username) based token?
Since you’re talking about an API it sounds like your asking “how can a headless process obtain an access token that will allow it to call the web api”?
LikeLike
Hi Sara,
I have an api which is secured by ad-b2c and I have 5 external clients consuming my api. I have registered these clients to b2c by creating 5 users. Now from their application, they want to consume my API. As you said, how would they obtain an access token? Since they are 2 different applications, I am assuming they will use some sort of unique keys/tokens.
Like the conventional way is to provide usernames and api keys to authenticate.
LikeLike