On the Policy window, you’ll see this Run Now button at the bottom of the screen.

The Policy – Run Now button opens the URL shown in the Run now endpoint (shown above the button) in a new tab browser. This call to B2C the /authorize endpoint displays the familiar login window.

Once you successfully login, B2C will send the token (either id_token or access_token) to the selected Reply URL listed on the Policy – Run Now page. If you add `https://jwt.ms` to one of your applications reply URLs, you’ll be able to select it from the dropdown.
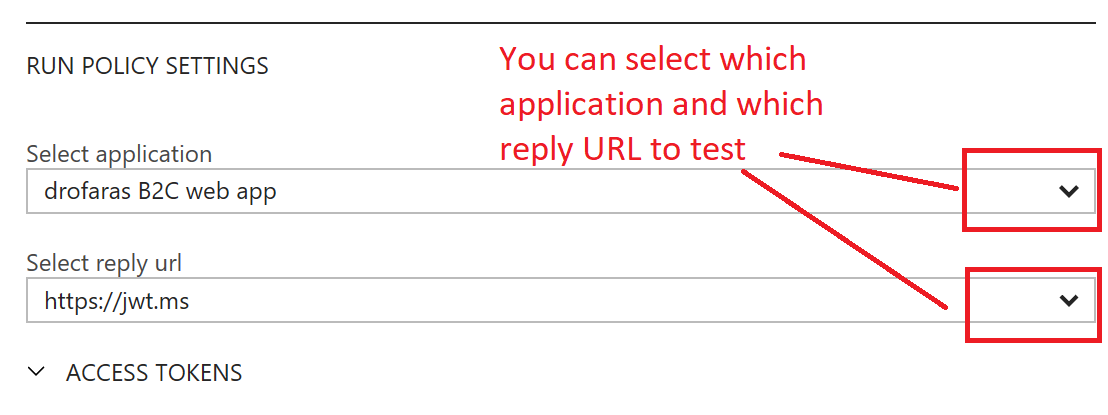
Recall you can add a reply URL to an application by going to its registration page, e.g. “drofaras B2C web app”, and adding https://jwt.ms to the list of Reply URLs.
Since this example requests an id_token be sent to https://jwt.ms, the following URL is shown in the browser.
https://jwt.ms/#id_token=eyJ0eXAiOiJKV1QiLCJhbGc...
I’ve learned that the # is a Fragment Identifier, so anything after the # can only be used client-side. The website jwt.ms takes this id_token and decodes it for you…

What about access tokens?
Yep, you can also test out access tokens as well as id tokens.
Go back to the Policy settings page and expand the Access Token area. Select the resource, e.g. a Web API, and the desired scopes you want to verify.

Clicking run now will open jwt.ms, but nothing will be displayed. The website is only looking for id_tokens. But, if you copy everything after the #access_token in the url
https://jwt.ms/#access_token=eyJ0eXAiOiJKV1QiL...
and paste that in directly to jwt.ms, you’ll see the access token decoded.
Other usages for Run Now
Suppose you’ve made some changes to your policy and you want to verify things are setup the way you want from within the Azure portal. Examples include
- You’ve added a sign-up claim and you want to verify this claim appears correctly in the id_token.
- You’ve added a new Social Identity Provider and want to quickly test you can sign in.
- You’ve added a new scope in the access token and want to verify it in your awaiting server listed in the Reply URL
Note
Something that confused me early on is I tried to test my policy immediately after I created it, meaning that I didn’t have a localhost server up and running yet. When I ran the policy, I got the following

Now of course this makes sense, since I’d need to have http://localhost:50185 (from image) running… however, I could have still verified my tokens by coping everything from the # token portion of the URL, e.g.
http://localhost:50185/#id_token=eyJ0eXAiOiJKV...
and pasting it into jwt.ms, even though my reply url server isn’t running.
FWIW
At first glance, I thought the Policy – Run Now button meant to “run” the policy as in “Visual Studio F5 Run” the policy – as if creating it, but that’s not what’s happening here.
At second glance, I thought the Run now button performed more logic behind the scenes, but it is just calling that /authorize endpoint in a new tab.
The #access_token is now supported too 🙂 So no more copy/pasting.
LikeLike
I was just about to say “I liked http://jwtinspect.azurewebsites.net/ would automatically take the token from the url”. Sounds like https://jwt.ms will do that now all tokens? Or only for #access_token’s?
LikeLike
nvm, I just ran a test and I can do the same thing w/ https://jwt.ms that I can do w/ http://jwtinspect.azurewebsites.net/
LikeLike